Configure RBAC for Connectors in Confluent Cloud
Role-based access control (RBAC) uses roles and role mappings to provide different levels of access for a principal to authenticate with Apache Kafka® and fully-managed connectors.
Note
RBAC for fully-managed and custom connectors is available for Standard, Enterprise, Dedicated, and Freight Kafka clusters only.
For self-managed connectors running in Confluent Platform, see RBAC for Self-Managed Connectors.
RBAC role mappings
Note
As of April 11, 2025, the Operator role no longer has permissions to pause and resume connectors. Confluent removed permissions to pause and resume connectors from the Operator role in Confluent Cloud, aligning with broad customer feedback. This change restores to administrators a read-only Operator role that can view metadata and monitor resources without the right to modify resources. You can grant users the ConnectManager role to monitor, pause, and resume connectors in your clusters.
RBAC role mappings for fully-managed connectors
The table below shows the RBAC role mappings for fully-managed connectors.
Role | Interact with Managed Connectors | Create a Data Preview Instance | View Data Preview Output | Read Configuration | Read Status | View Logs | Read Throughput Metrics | Pause, Resume, and Restart | Configure | Configure Kafka Credentials | Manage Access | Delete |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
No | No | [1] | No | Yes | No | Yes | Yes | No | No | No | No | |
Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
No | No | [1] | Yes | Yes | Yes | Yes | Yes | No | No | No | No | |
No | No | [1] | Yes | Yes | No | Yes | No | Yes | No | No | No | |
No | No | [1] | Yes | Yes | No | Yes | No | No | No | No | No |
[1] The role can view the data preview output only if the role has READ access to the data preview topic.
Certain Confluent Cloud RBAC roles are currently unavailable for fully-managed custom connectors. For the full list of RBAC roles and role mappings used for Confluent Cloud, see Predefined RBAC Roles in Confluent Cloud. For additional information, see Role-based Access Control (RBAC) on Confluent Cloud.
RBAC role mappings for custom connectors
The table below shows the RBAC role mappings for custom connectors.
Users/Service Account | Scope | Assign Access to users on Custom Connectors (Not Artifacts) | Upload Artifact | Edit/Update Artifact | List/Describe Artifacts | Delete Artifacts | Create Custom Connector | Edit Custom Connectors | List/Describe Custom Connectors | Delete Custom Connectors | Read Custom Connector Status | Read Custom Connector Metrics | Pause/Resume/Restart Custom Connectors | View Custom Connector Logs |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Organization | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
Environment | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | |
CloudClusterAdmin “[1]” | Cluster | Yes | No | No | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
Organization/Environment/Cluster | No | No | No | No | No | No | No | Yes | No | Yes | Yes | No | No | |
Connector(s) | No | No | No | No | No | No | No | Yes | No | Yes | Yes | No | No | |
Connector(s) | No | No | No | No | No | No | Yes | Yes | No | Yes | Yes | Yes | No | |
Connector(s) | No | No | No | No | No | No | No | Yes | No | Yes | Yes | Yes | Yes | |
Connector(s) | Yes | No | No | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
[1] CloudClusterAdmin role has different permissions based on the resource (Connect API vs CCPM API). The role mapping in this table is valid for CCPM APIs as it does not allow Cluster Admins to create, edit or delete plugins.
Manage role assignments using the Cloud Console
Complete the following steps to configure a role assignment for a user or service principal. You must have administrative permissions to work with role assignments.
Open the Administration menu.
Select Accounts & access.
Select Access.
Select the cluster where you want to configure connector permissions, then click Connectors. You may see one or more assigned roles.
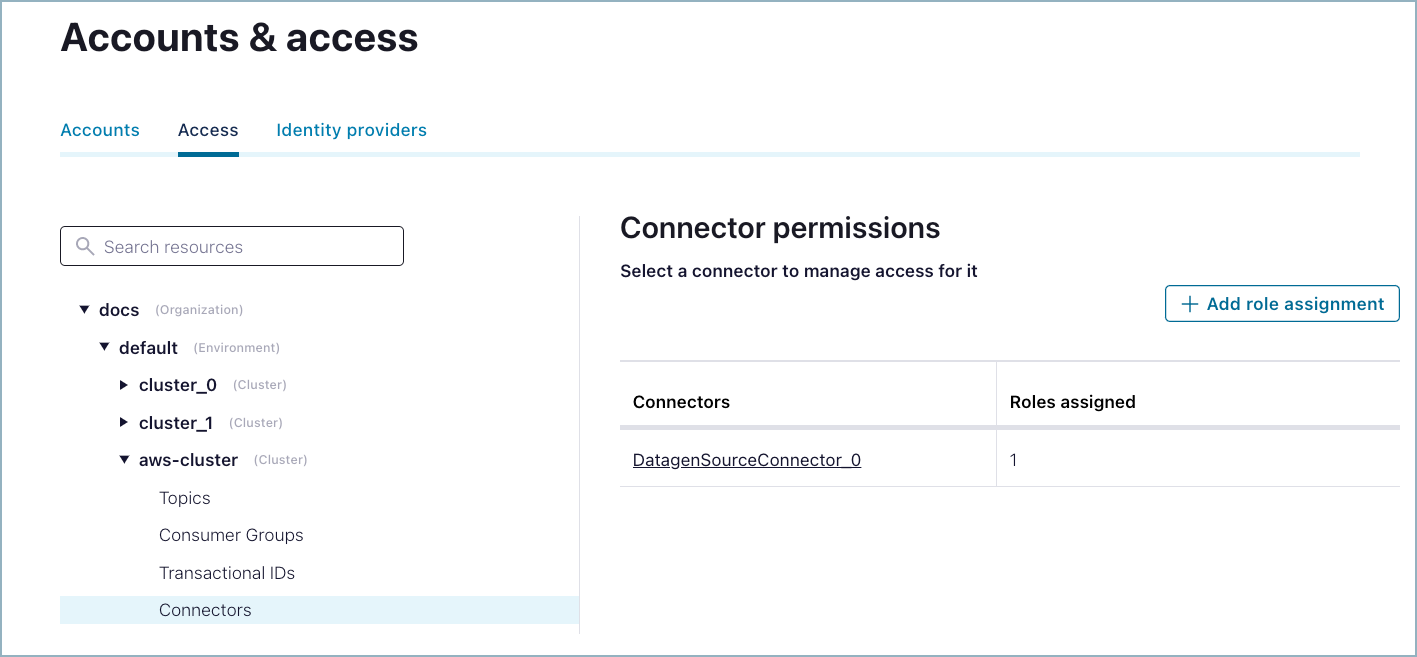
Connector permissions
The following message may be displayed if you have no connector role assignments in the cluster.

No role assignments
Add a new role assignment
Complete the following steps to add a role assignment.
Click the Add role assignment button.
Select an existing connector name. You can enter a new connector name here. This allows you to create the role assignment prior to creating the connector.
Select the account where you want to apply the role assignment.
Select DeveloperRead or DeveloperWrite. For specific permissions and other details, see RBAC role mappings.
Click Save.
Delete a role assignment
To delete a role assignment, click a listed account name and then click the trash can icon. Only administrative roles can delete a role assignment.
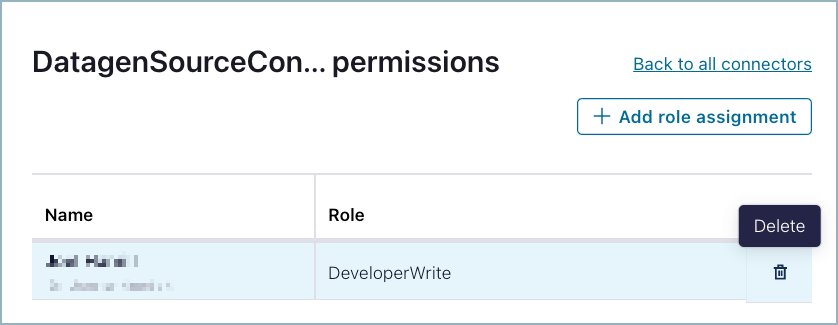
Delete assignment
Manage role assignments using the Confluent CLI
The following are typical commands to use when managing role assignments for fully-managed connectors.
To see the available command options:
confluent iam rbac role-binding help
To list the role assignments:
confluent iam rbac role-binding list --current-user
confluent iam rbac role-binding list --principal User:u-12ab34
To create a role assignment:
confluent iam rbac role-binding create --principal User:u-12ab34 \
--role DeveloperWrite --resource DatagenSourceConnector_0 \
--environment env-a12b34 --kafka-cluster-id lkc-123456
To delete a role assignment:
confluent iam rbac role-binding delete --principal User:u-12ab34
For additional Confluent CLI command examples, see List the role bindings for a principal.