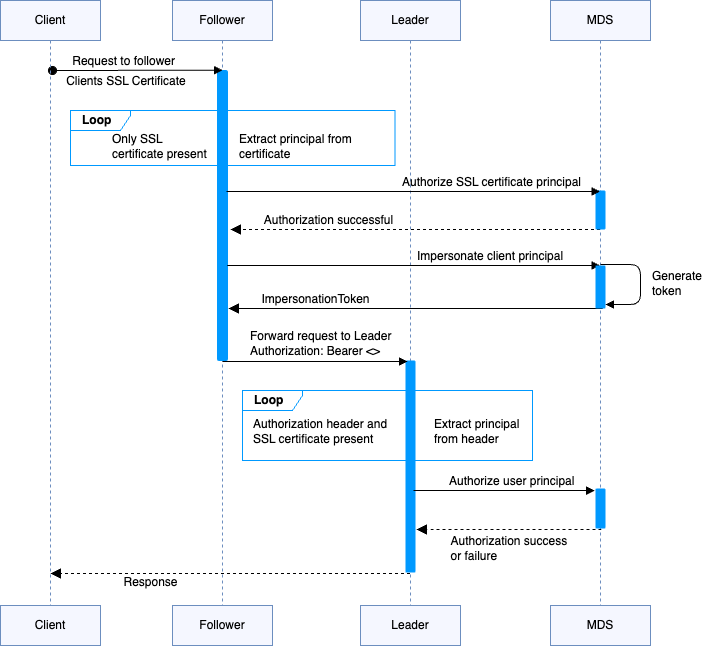
Request Forwarding from Follower to Leader in Confluent Platform
On this page you’ll find an explanation of request forwarding from follower to leader in role-based access control (RBAC) without and with mTLS authentication.
Impersonation controls
You must set mandatory properties on the MDS server that prevent others from impersonating specific principals. You can also list the principals that can impersonate others.
To enable request forwarding with mTLS, you must provide both the list of protected users and the list of users allowed to impersonate others.
Mandatory impersonation protection
List the protected, privileged identities that others can’t impersonate for security reasons, for example:
confluent.metadata.server.impersonation.protected.users=User:<rp-principal-name>;User:<other-super-user>
You should always include super users in the list of protected users.
Who can impersonate
List the users that can impersonate a targeted user, for example:
confluent.metadata.server.impersonation.super.users=User:<rp-principal-name>;User:<sr-principal-name>;User:<connect-principal-name>;User:<other-super-user>
You can allow impersonation for specific service identities to enable request forwarding from followers to leaders. For example, multi-node Schema Registry or Connect clusters. Add the following configuration to MDS, specifying the service identities permitted to impersonate other users, replacing <service-identity1> and <service-identity2> with the actual service identities:
confluent.metadata.server.impersonation.super.users=User:<service-identity1>;User:<service-identity2>