Metadata Service (MDS) as Token Issuer in Confluent Platform
When you use Metadata Service (MDS) with role-based access control (RBAC) in your Confluent Platform configuration, you can use MDS as the token issuer for client authentication and authorization. Clients can be Kafka clients, applications, or users through interfaces. As token issuer, MDS supplies JWT tokens in response to authentication requests from clients.
When RBAC is enabled with LDAP authentication, the MDS issued tokens are used by clients for authentication and authorization.
When you enable RBAC with OAuth on the Confluent Platform cluster, the MDS issued tokens are primarily used for authorization requests. All client authentications are handled by the services without requiring MDS. For user authentications using single-sign on (SSO), the identity provider (IdP) handles authentications.
You can leverage MDS capabilities along with RBAC so that different authentication mechanisms can coexist within your Confluent Platform cluster. One set of clients can authenticate via MDS-issued tokens and another set through OAuth tokens because the AuthenticationHandler in REST interfaces accepts both MDS and IdP issued tokens. This dual token support means you can upgrade your Confluent Platform from LDAP to OAuth authentication with minimal disruption to existing workflows as clients or services that haven’t migrated to OAuth can continue to operate.
Example of MDS and IdP tokens in use
Consider the following diagram that illustrates the Confluent CLI SSO flow. This flow illustrates how Confluent Platform use both MDS issued tokens and identity provider (IdP) issued tokens:
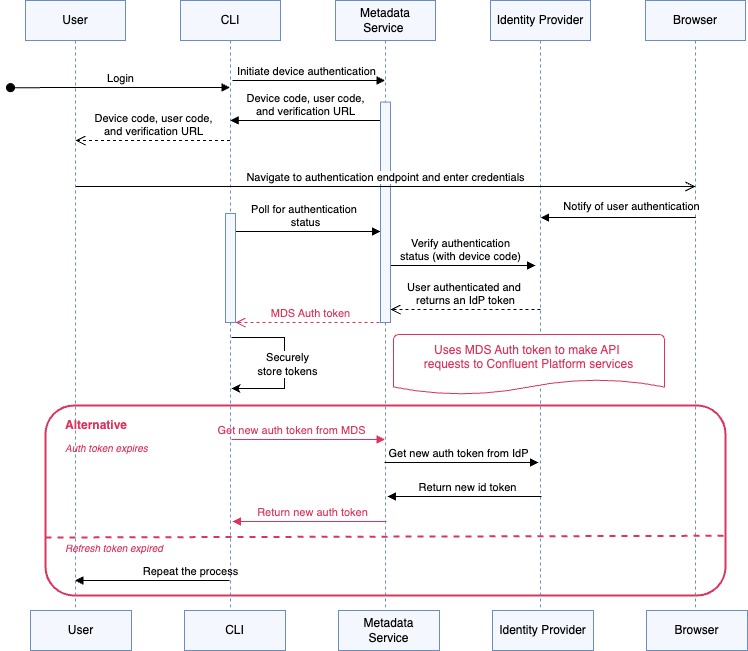
The Confluent CLI uses device grant flow. MDS acts as the intermediary that enables a flow where MDS interacts primarily with the IdP and the CLI never directly interacts with the IdP.
Once the end-user authentication succeeds with the IdP, MDS issues a token to the CLI. This MDS token is built on top of the IdP issued token and contains the identity information of the end user. For further authentication requests with other Confluent Platform services the CLI continues to use the MDS token instead of the IdP issued token.
When the MDS token expires, the CLI authenticates to MDS, and MDS authenticates to the IdP to fetch a new IdP token upon which it builds a new MDS token. MDS returns its new token to the Confluent CLI.