Use OAuth/OIDC for Authentication in Confluent Platform
Confluent Platform provides support for OAuth/OIDC-based authentication, based on the OAuth (Open Authorization) 2.0 industry standard protocol for authorization and extended using OIDC (OpenID Connect) support for authentication. Newly added OAuth capabilities are built to work with other existing enterprise security features of the Confluent Platform. There are many ways to leverage the new OAuth/OIDC support in Confluent Platform, along with other enterprise capabilities for authorization, encryption, and identity provider protocols. For a comprehensive overview of the different options available for use with OAuth, see Security Deployment Profiles in Confluent Platform.
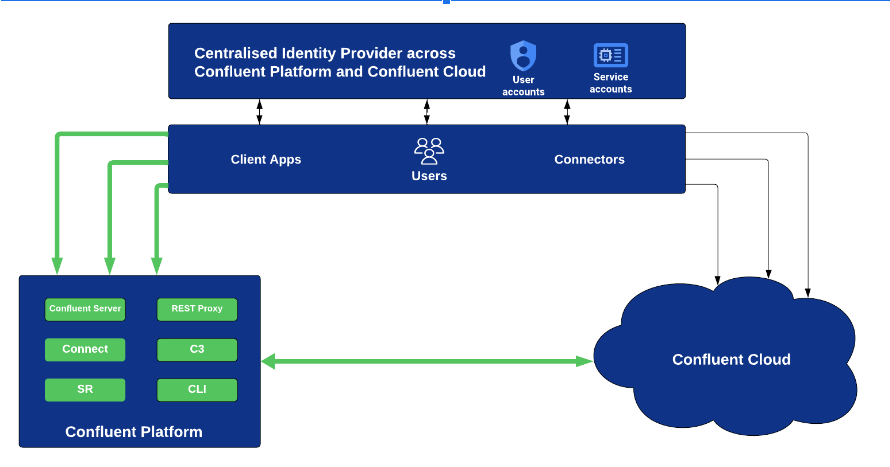
The Confluent Platform 7.7 release adds OAuth/OIDC authentication capabilities to Confluent Platform services, including Confluent Server (SASL/OAuthBearer), Schema Registry, Confluent Community, Connect, REST Proxy, and Confluent CLI.
Use OAuthBearer for authentication for a wide range of capabilities across the Confluent Platform:
Client to Confluent Platform services (Confluent Server (SASL/OAuthBearer), Schema Registry, and REST Proxy).
Service-to-service communication between different Confluent Platform services, such as between a Confluent Server broker and Schema Registry, Connect to Schema Registry or Connect to a Confluent Server broker. When deployed between two Confluent Platform services, OAuthBearer functionality uses the client credentials grant flow similar to KIP-768.
For hybrid features like Schema Linking between Schema Registry in Confluent Platform clusters and Schema Registry in Confluent Cloud clusters. And, self-managed connectors authentication to Confluent Cloud.
Connector authentication to Confluent Platform services.
Two different identity providers can be supported to work together with the Confluent Platform on OAuth/OIDC to isolate user identities and workload identities.
Use OIDC SSO (single sign-on) for authentication to all Confluent Platform interfaces:
SSO for Confluent Control Center (without any dependencies on LDAP).
SSO for Confluent CLI.
OIDC-based bearer token authentication to REST interfaces of Confluent Platform services.
With Confluent Platform 7.7, all identities across Confluent Platform workloads and interfaces can be hosted on a single identity provider providing for a unified identity management solution. And, it is not required to deal with duplicate service accounts, principals representing one identity. Use Confluent for Kubernetes and Ansible Playbooks for Confluent Platform to deploy all the above capabilities.