Use the AuthenticationHandler Class for Multi-Protocol Authentication in Confluent Platform
Starting with Confluent Platform 7.7, a new handler class, AuthenticationHandler, is available only for REST-based services, including Schema Registry, Kafka REST, and Connect.
The AuthenticationHandler handler class is designed to accept:
Identity provider (IdP) OAuth tokens
Confluent OAuth tokens provisioned by MDS
HTTP Basic Authentication
HTTP Basic Authentication using LDAP usernames and passwords
Mutual TLS (mTLS) certificates
By accepting multiple authentication mechanisms, the AuthenticationHandler handler enables REST-based services in Confluent Platform to:
Upgrade from existing non-OAuth authentication mechanisms to support OAuth authentication without any downtime.
Simultaneously support multiple protocols based on your application requirements.
The AuthenticationHandler can simultaneously handle requests from:
Existing legacy clients that use:
LDAP usernames and passwords
MDS tokens
New clients that use:
OAuth tokens
Mutual TLS (mTLS) certificates
Both OAuth tokens and mTLS certificates
The AuthenticationHandler class can also provision metrics for each of the different authentication types.
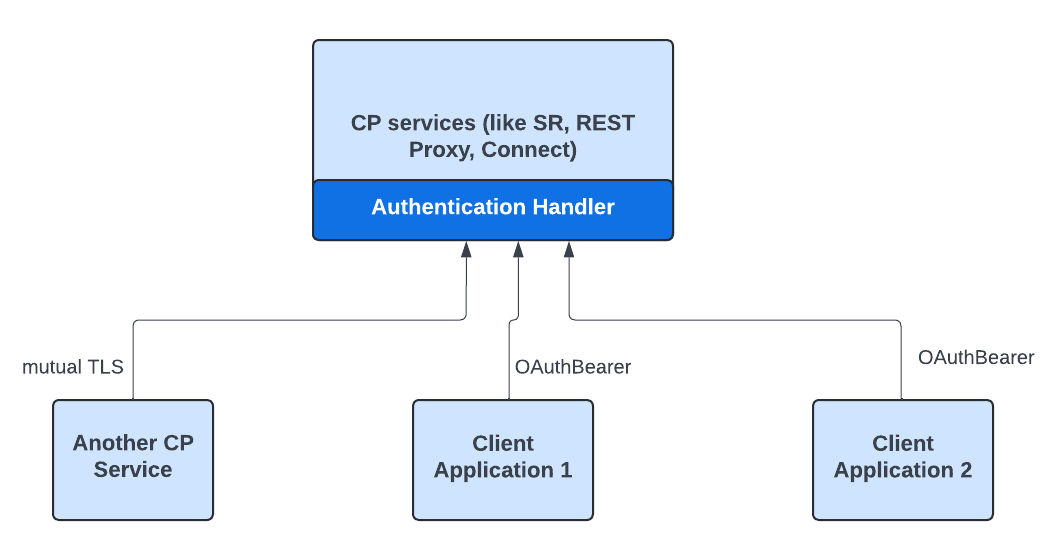
Example of multi-protocol authentication in Confluent Platform
The diagram below illustrates an example of how the AuthenticationHandler class in Confluent Platform allows for flexible authentication for REST-based services by accepting multiple authentication mechanisms. Note the following:
The
AuthenticationHandlerclass authenticates requests from multiple protocols, in this example, OAuth 2.0 and mTLS.Application Client 1 and 2 use OAuth 2.0 to authenticate with the Confluent Platform services. The
AuthenticationHandlerclass processes the OAuth tokens, verifies them, and provides access based on their validity, and the permissions granted.Application Client 3 uses mTLS to authenticate with the Confluent Platform services. In this setup, both the client and server authenticate each other using certificates. The
AuthenticationHandlerclass verifies the client certificates, ensuring both the client and server are trusted entities.
Use the AuthenticationHandler class
You can use the AuthenticationHandler class for multi-protocol authentication in your Confluent Platform cluster by adding the following property:
rest.servlet.initializor.classes
Configuration examples
Following are examples of how to configure the AuthenticationHandler class for supported authentication mechanisms. Adjust the property values according to your specific environment and requirements.
Identity provider (IdP) OAuth tokens
To configure the AuthenticationHandler for IdP OAuth tokens:
rest.servlet.initializor.classes=io.confluent.common.security.jetty.initializer.AuthenticationHandler
authentication.method=OAUTH
oauth.jwks.endpoint.url=https://your-idp.com/.well-known/jwks.json
oauth.valid.issuer=https://your-idp.com
oauth.expected.audience=your-audience
Confluent OAuth tokens
For Confluent OAuth tokens from Confluent Cloud:
rest.servlet.initializor.classes=io.confluent.common.security.jetty.initializer.AuthenticationHandler
authentication.method=OAUTH
oauth.jwks.endpoint.url=https://confluent.cloud/.well-known/jwks.json
oauth.valid.issuer=https://confluent.cloud
oauth.expected.audience=your-confluent-cloud-audience
HTTP Basic Authentication
To use HTTP Basic Authentication:
rest.servlet.initializor.classes=io.confluent.common.security.jetty.initializer.AuthenticationHandler
authentication.method=BASIC
basic.auth.user.info=user1:password1,user2:password2
HTTP Basic Authentication using LDAP usernames and passwords
For HTTP Basic Authentication with LDAP:
rest.servlet.initializor.classes=io.confluent.common.security.jetty.initializer.AuthenticationHandler
authentication.method=BASIC
basic.auth.ldap.url=ldap://your-ldap-server:389
basic.auth.ldap.user.base.dn=ou=users,dc=example,dc=com
mTLS
To configure mTLS:
rest.servlet.initializor.classes=io.confluent.common.security.jetty.initializer.AuthenticationHandler
authentication.method=TLS
ssl.client.auth=required
ssl.truststore.location=/path/to/truststore.jks
ssl.truststore.password=truststore-password
ssl.keystore.location=/path/to/keystore.jks
ssl.keystore.password=keystore-password
Monitoring authentication
It’s useful to get the monitoring data of authentication requests, their success rates, and associated latencies. You can enable monitoring of authentication through the AuthenticationHandler. This class generates metrics for the different Confluent Platform authentication mechanisms, OAuth, mTLS, basic, and MDS over OAuth.
To enable monitoring, set this property in the Confluent REST Proxy service:
rest.auth.jmx.enabled=true
You should begin to see metrics similar to the following:
Total successful auth requests
Total unsuccessful auth requests
Latency in successful auth request ( sampled )
Latency in un successful auth request (sampled )
Average latency of successful auth requests ( ms )
Max latency of successful auth requests (ms).
99 percentile of latency for successful auth requests (ms)
95 percentile of latency for successful auth requests (ms)
Confluent Platform uses JMX (Java Management Extensions) for exposing metrics from various services, including the Confluent REST Proxy. This allows you to monitor with Confluent Control Center or external tools like JConsole, Prometheus, and Grafana. For more information using these tools with Confluent Platform, see Monitor Consumer Lag in Confluent Platform.