重要
このページの日本語コンテンツは古くなっている可能性があります。最新の英語版コンテンツをご覧になるには、こちらをクリックしてください。
RBAC for Managed Connectors¶
注釈
For self-managed connectors running in Confluent Platform, see RBAC for Self-Managed Connectors.
Role-based access control (RBAC) uses roles and role mappings to provide different levels of access for a principal (user or service) to authenticate with Apache Kafka® and managed connectors.
注釈
RBAC for managed connectors is available for Standard and Dedicated clusters only.
Connector RBAC role mappings¶
The table below shows the RBAC role mappings for managed connectors.
| Role | Create a Connector | Create a Data Preview Instance | View Data Preview Output | Read Configuration | Read Status | View Logs | Read Throughput Metrics | Pause and Restart | Configure | Configure Kafka Credentials | Manage Access | Delete |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| OrganizationAdmin | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| EnvironmentAdmin | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes |
| CloudClusterAdmin | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes |
| Operator | No | No | [1] | No | Yes | No | Yes | Yes | No | No | No | No |
| DeveloperRead | No | No | [1] | Yes | Yes | No | No | No | No | No | No | No |
| DeveloperWrite | No | No | [1] | Yes | Yes | No | No | No | Yes | No | No | No |
- Note:
- [1] The role can view the data preview output only if the role has
READaccess to the data preview topic.
Certain Confluent Cloud RBAC roles are currently unavailable for managed connectors. For the full list of RBAC roles and role mappings used for Confluent Cloud, see Confluent Cloud RBAC ロール. For additional information, see Confluent Cloud でのロールベースアクセス制御(RBAC)の使用.
Manage role assignments using the Cloud Console¶
重要
You must have administrative permissions to work with role assignments.
Complete the following steps to configure a role assignment for a user or service principal.
Open the Administration menu.
Select Accounts & access.
Select Access.
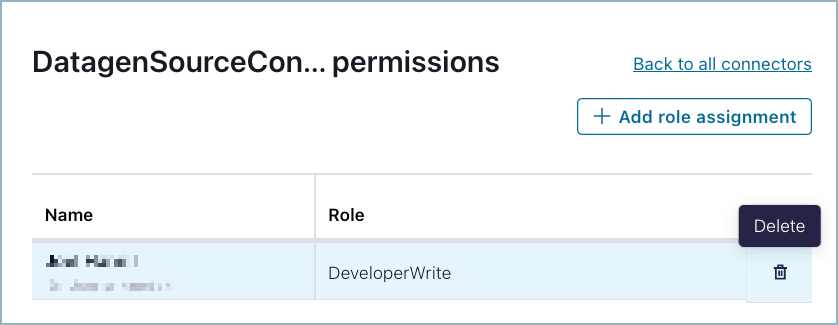
Select the cluster where you want to configure connector permissions, then click Connectors. You may see one or more assigned roles.
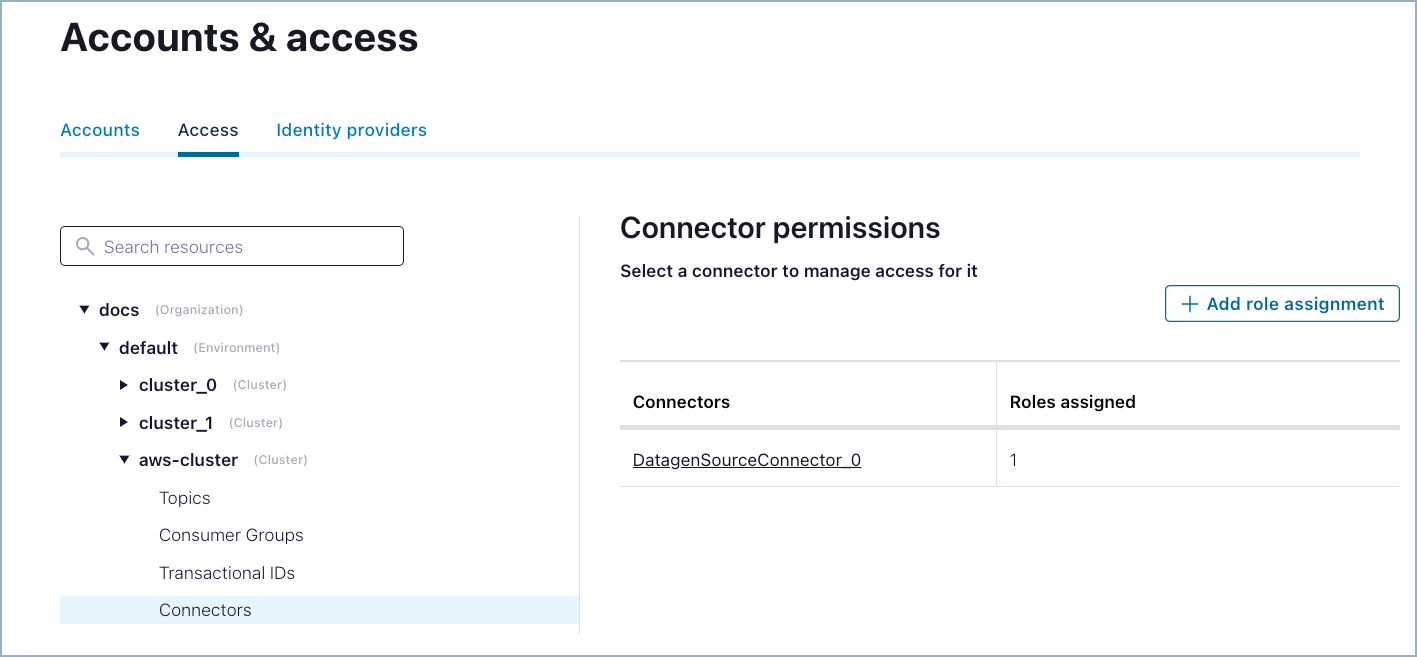
Connector permissions¶
The following message may be displayed if you have no connector role assignments in the cluster.
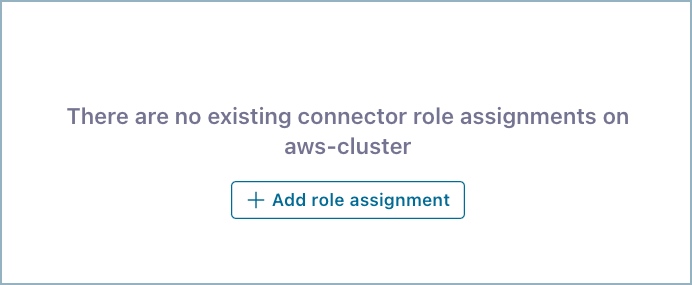
No role assignments¶
Add a new role assignment¶
Complete the following steps to add a role assignment.
- Click the Add role assignment button.
- Select an existing connector name. You can enter a new connector name here. This allows you to create the role assignment prior to creating the connector.
- Select the account where you want to apply the role assignment.
- Select DeveloperRead or DeveloperWrite. For specific permissions and other details, see Connector RBAC role mappings.
- Click Save.
Manage role assignments using the Confluent CLI¶
The following are typical commands to use when managing role assignments for managed connectors.
To see the available command options:
confluent iam rbac role-binding help
To list the role assignments:
confluent iam rbac role-binding list --current-user
confluent iam rbac role-binding list --principal User:u-12ab34
To create a role assignment:
confluent iam rbac role-binding create --principal User:u-12ab34 \
--role DeveloperWrite --resource DatagenSourceConnector_0 \
--environment env-12345 --kafka-cluster-id lkc-123456
To delete a role assignment:
confluent iam rbac role-binding delete --principal User:u-12ab34
For additional Confluent CLI command examples, see Confluent CLI を使用した RBAC の管理.